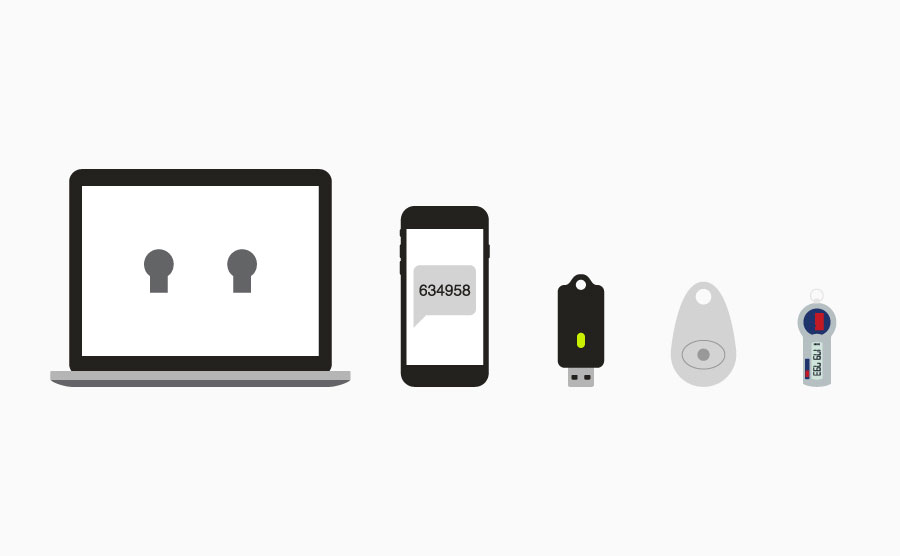
It’s important to ensure you’re in control of your accounts.
Using traditional username and password authentication (one-factor), it’s relatively easy for a hacker to break into your account. The largest number of attacks are possible against one-factor authentication, including brute force, dictionary, man-in-the-middle, and phishing attacks. That’s why we recommend using two-factor authentication.
Two-Factor Authentication
Two-factor authentication (2FA) increases your control by requiring two pieces of evidence to log in. The first piece of evidence is usually knowledge of a password. The second piece of evidence can be either possession of a device (e.g., a smartphone that receives SMS codes or a U2F security key) or biometrics (e.g., fingerprint or voice). This adds an extra layer of security that protects you and your accounts in case your password is compromised.
Let’s explore the most popular forms of 2FA that you can use to secure your accounts today: SMS, OTP, and FIDO U2F.
Short Message Service
Short message service (SMS) is commonly known as text messaging.
Many services can send you SMS messages whenever you log into your account. These messages contain a one-time code you’ll enter on the service’s login page to prove you have possession of your phone. With this system, your phone is used as the second factor of authentication. This makes it tougher for attackers trying to hack your account as they need your password and SMS code.
Unfortunately, attackers can use SIM swap attacks to redirect your text messages to their phone or intercept them using flaws in the cellular network. SMS 2FA, while convenient, is among the weakest forms of 2FA available. However, it’s still better than using just a username and password.
Similar to SMS 2FA is phone call-based 2FA, which sends you a code to your phone by voice message. The setup and login follows the same process for SMS 2FA and suffers the same weaknesses.
Here’s a demonstration of an SMS 2FA attack.
One Time Passwords
One time passwords (OTP) are generated codes that are valid for a short time or a single login, and are commonly provided through a smartphone app. OTP is also referred to as a software token.
To set up OTP, the service generates a secret key (a long string of random numbers and letters), which you save to your smartphone app by copying and pasting the key or scanning a generated QR code. After this, the phone and server both have a copy of the secret key.
To log in, you must enter your username, password, and OTP code, which your app generates using the secret key.
There are two types of OTP: TOTP (time-based one time passwords) and HOTP (HMAC-based one time passwords). TOTP codes are generated using the secret key and the current time, while HOTP codes are generated using the secret key and a counter that tracks the number of times the HOTP code is used. TOTP codes change more frequently than HOTP codes, which is why they’re considered the more secure OTP option.
While more secure than SMS 2FA, OTP are still vulnerable to man-in-the-middle and phishing attacks.
FIDO Universal 2nd Factor
FIDO Universal 2nd Factor (FIDO U2F) is an open authentication standard that uses specialized USB or NFC (near-field communication) security keys based on public key cryptography. It’s also referred to as a hardware token.
To set it up, you register your FIDO U2F security key with the service. Your security key will generate a private and public key pair, and send the public key to the service. When you log in to the service on a new computer, the service will ask you to plug in your security key or press a button on it. When you do so, the service sends a challenge to your security key, your security key signs it using the private key, and the service verifies if the signed challenge is correct using the public key. This ensures that you have possession of the security key that you registered.
FIDO U2F is the most secure form of 2FA that prevents against password cracking, man-in-the-middle, and phishing attacks.
Learn more about FIDO U2F here.
Conclusion
There are many forms of 2FA, some of which are stronger than others. Nonetheless, using even the weakest form of 2FA is better than using none. Not every service supports every form of 2FA, so you should use the strongest one available based on the technology you have. You should always use FIDO U2F if you can; if not, use OTP; if that isn’t available, use SMS. If none are available, you’ll have to settle for using a strong password.
Bluink Key provides FIDO U2F, OTP, and a password manager that lets you easily use strong passwords so that you always have the strongest authentication regardless of what forms of 2FA your services support.